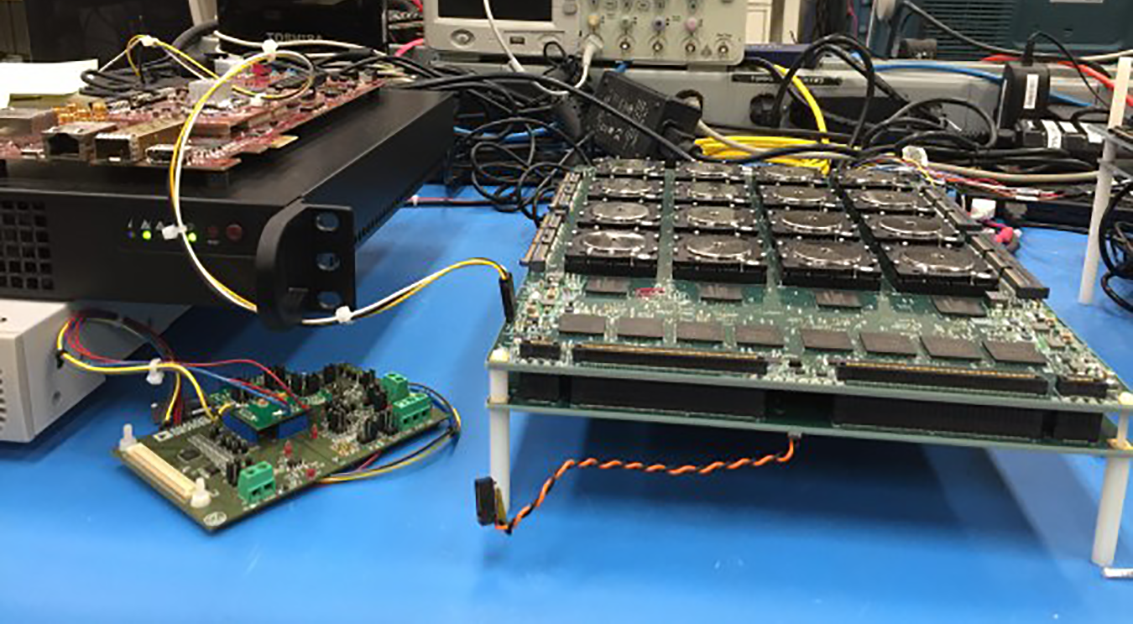
Third-Party cores are commonly used as integral parts of system-on-chips. Outsourced production at non-trusted facilities opens the door for hardware trojan insertion to critical system-on-chips. Hardware trojan Intrusion can occur in any of the design, verification and manufacturing stages even without the intention of the primary producer. Moreover, post-fabrication testing based on side-channel observation tests are ineffective to detect hidden trojans in complex system-on-chips with dozens of inputs, outputs, states, and memory blocks. Thus, the detection of malicious components before system deployment is particularly crucial for a system integrity and safety.
At Belpico, we are developing new hardware trojan sandboxing technologies for system-on-chips. Our technology contains non-trusted components in the isolated virtually resourced area and protects the rest of the system against damage. Meanwhile, the rest of the trusted components have access to any system resource. Furthermore, overall power behaviour, temperature profile, path delays, and other physical parameters are carefully monitored by side-channel analyses. Since hardware trojans have a noticeable impact on the physical properties of the system, activation of hardware trojan in trusted components is detected by side-channel analyses.
Please feel free to contact us if you need any further information.
Start Now
Air Defence SystemsMicrowave generators for future high power electromagnetic air defence systems.

Cybersecurity Consultancy and Audit Services We focus on the quality of the working relationship between our security auditing and information security functions.

Space Force Logistics and ModernizationHard rebooting, refuelling, maintenance, and part replacement of compatible satellites in-orbit.
MicroelectronicsContain non-trusted components in the isolated virtually resourced area.
Radar and Electronic WarfareOur mode-locked laser generates tunable microwaves with ultralow phase noise.